OWASP API Security Access Control Model
- OWASP
- Access Control Model
- API Security
Yo, in today’s world, web apps ain’t just static pages anymore—they’re beasts with complex access control setups. Devs gotta set up tight permissions so users don’t go where they shouldn’t. That’s where API security comes in: keeping stuff locked down while still letting legit users do their thing.
What’s an Access Control Model?
Think of it as the bouncer for your API. It decides who gets in, what they can touch, and how much power they have. In a web app, this model defines the rules based on user roles. Like, an admin gets the golden key to everything, but a regular user? Nah, they only get what they need—no VIP access.
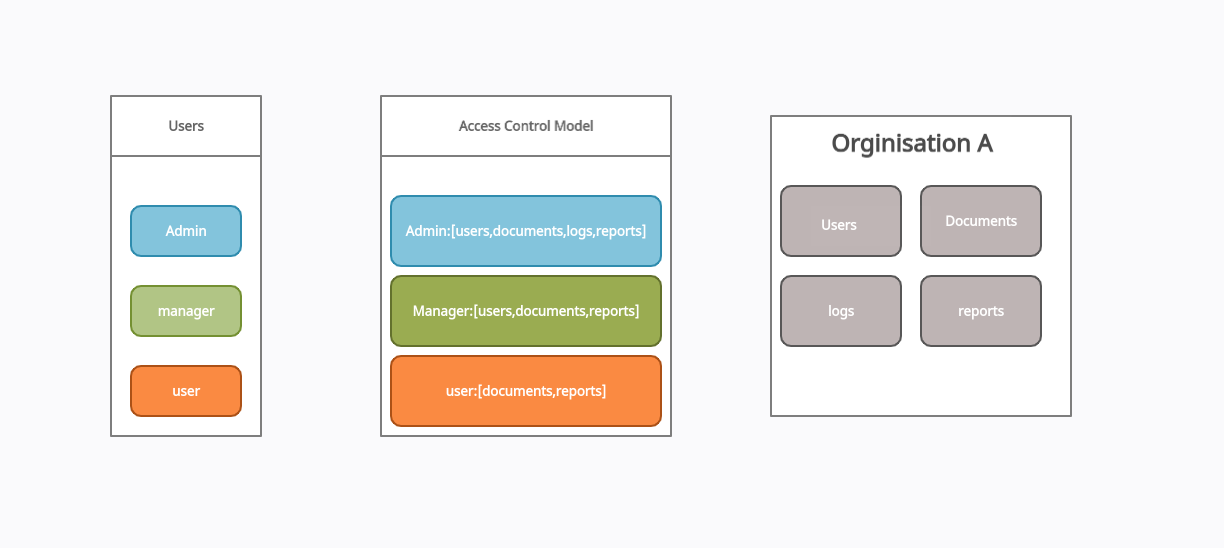
A classic example is Role-Based Access Control (RBAC)—where users get permissions based on their role. Picture this:
- Admin: Gets access to
All(users, documents, logs, and reports). Basically, they run the show. - Manager: Can mess with
users,documents, andreports, but logs? Not their business. - Regular User: Just here to see
usersanddocuments, no funny business.
Alright, now let’s break down the common types of Access Control Models:
- RBAC (Role-Based Access Control): Keeps it simple by grouping users with similar access needs. No need to micromanage every single user.
- DAC (Discretionary Access Control): The asset owner decides who gets in. More flexibility, but also more room for screw-ups.
- MAC (Mandatory Access Control): Used in high-security environments (think gov/military). Data is labeled like
confidential,secret,top-secret, and only the right peeps get access.
Broken Access Control: The Big Oops
Web apps are getting wild, and security ain’t getting any easier. When access controls aren’t set up right, you get Broken Access Control—basically, an all-you-can-eat buffet for attackers. They slip in and get their hands on restricted info. Not a good look.
Classic Access Control Fails
Mess up your access control, and you’ve got some real problems. Here are the usual suspects:
- Permissions Gone Wrong: If
/api/usersneedsread:users, but an attacker can still get in without it? Yeah, you got a problem. - Permission Clash: One permission accidentally overrides another. Like, if
read:userssneakily gives access to/api/reportstoo? Whoops. - Weird Permission Combos: Some funky mix of permissions unlocks extra access by accident. Like
read:X+read:Ysomehow also givingread:Z? Yikes.
The real challenge? Testing for all these mess-ups before someone else finds them first.
Breaking Access Controls (Like a Pro, But Ethically)
Now, let’s talk about testing these bad boys. Security pros have a few tricks up their sleeves to spot broken access control:
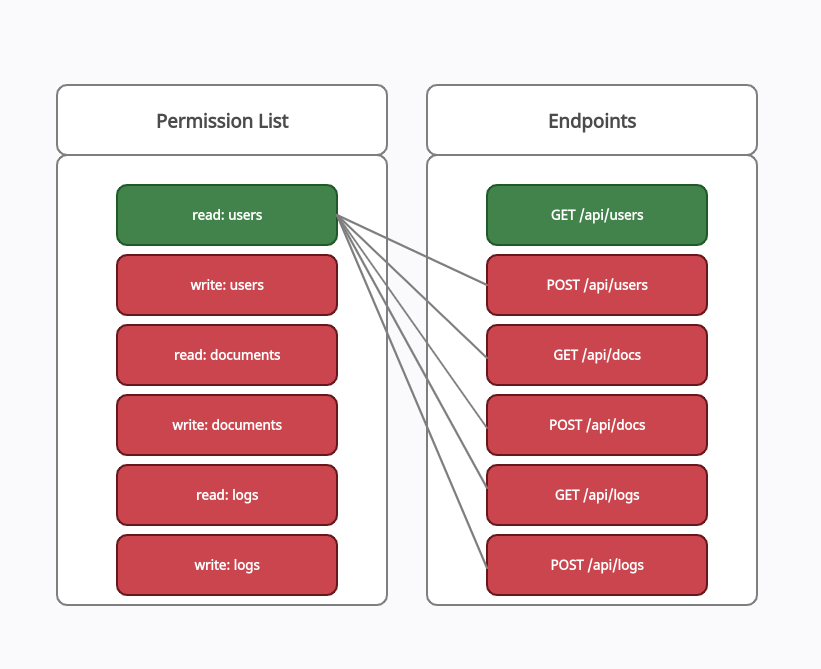
- Forward Approach: Start with just one permission and test if you can sneak into restricted areas.
Example of Forward Approach:
Give a user read:users, then see if they can wander into unauthorized API endpoints.
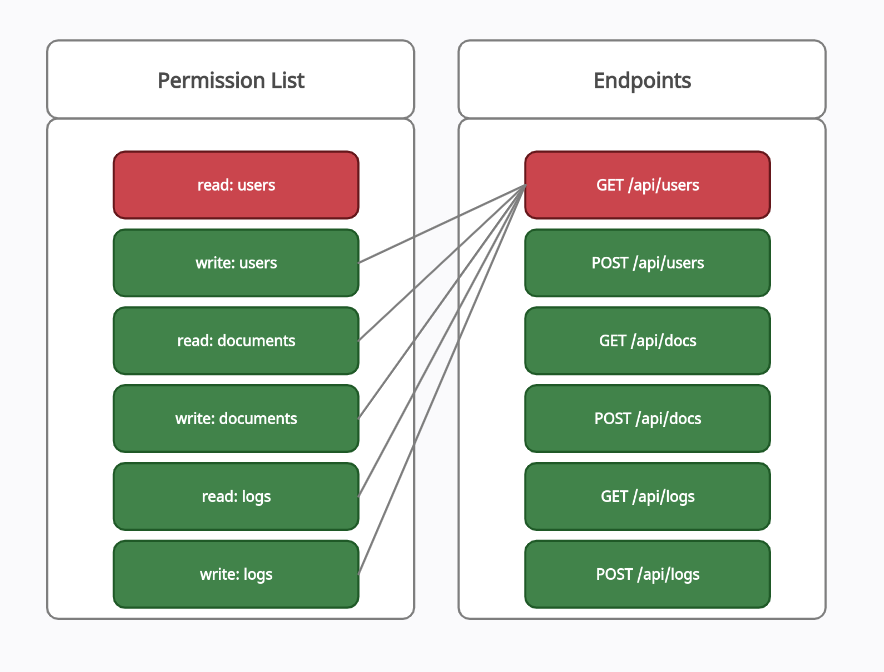
- Backward Approach: Give a user all permissions except one, then check if they’re locked out of what they should be.
Example of Backward Approach:
Take away read:users, then see if they can still pull user data from GET /api/users.
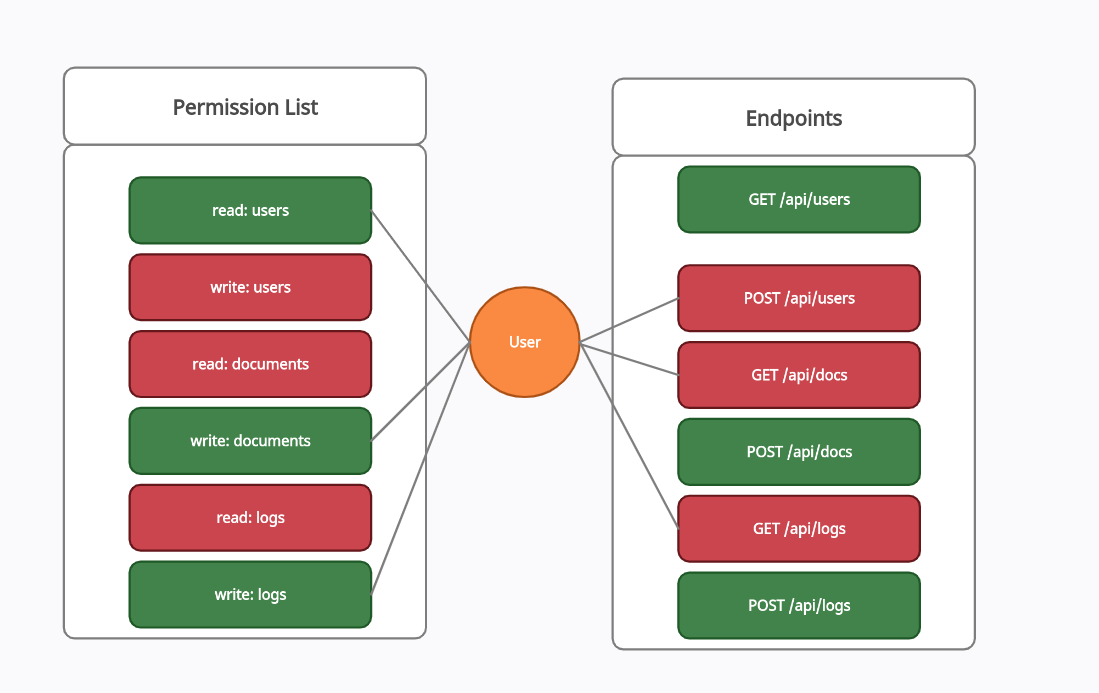
- Mixed Approach: Throw in a random mix of permissions and see if it leads to unexpected access. It’s like stress-testing the system for accidental privilege escalations.
Example of Mixed Approach:
A user with read:users, write:docs, and write:logs should not be able to access restricted API endpoints. But can they?
Final Thoughts
Locking down APIs means keeping everything scoped properly—no loose ends. Stuff like Insecure Direct Object References (IDOR) is just one type of access control fail, but trust me, there are plenty more ways to screw it up.
Got questions, wanna nerd out about API security? Hit me up:
Catch ya later.
How am I doing?
Hey! Lemme know if you found this helpful by leaving a reaction.
- x0
- x0
- x0
- x0
- x0
- x0
- x0
Loading