Security Posture Assessment
- Identify
- Detect
Methodology
The security assessment focused on evaluating vulnerabilities within the target system's web application component. This included an examination of the application's source code, configurations, and user interactions. The assessment also encompassed the underlying infrastructure, database, and session management mechanisms. However, it's important to note that the assessment did not cover the network perimeter, physical security, or external dependencies outside the scope of the application.
List of Findings and Severity:
| Finding | Severity |
|---|---|
| SQL Injection | High |
| Cross-Site Scripting (XSS) | Medium |
| Insecure Auth. & Session Mgmt. | Critical |
| Directory traversal | High |
| OS command injection | Critical |
| Business logic | High |
| Information Disclosure | Medium |
| Access Control | High |
| File Upload | Critical |
| Race conditions | Medium |
| Server-side request forgery | High |
| XML External Entity | High |
| Cross-site request forgery | Medium |
| Cross-origin resource sharing | Medium |
| Clickjacking (UI redressing) | Medium |
| DOM-based | High |
| WebSockets | Medium |
| GraphQL API | High |
| Server-side template injection | High |
| Web cache poisoning | High |
| HTTP Host header attacks | Medium |
| HTTP request smuggling | High |
| OAuth 2.0 authentication | High |
| Prototype pollution | High |
| JWT attacks | High |
Details for Each Finding:
SQL Injection
The SQL Injection vulnerability discovered in the target system arises from improper input validation in user-provided data. Attackers can exploit this vulnerability to execute malicious SQL queries, potentially gaining unauthorized access to the database or altering data. The absence of input sanitization exposes the application to this risk.
Proof of Concept (PoC):
- Input:
'; DROP TABLE users; -- - Resulting Query:
SELECT * FROM products WHERE name = ''; DROP TABLE users; --'
References:
- OWASP SQL Injection
- CWE-89: Improper Neutralization of Special Elements used in an SQL Command ('SQL Injection')
Risk/Severity Scoring:
- CVSS Base Score: 8.5 (High)
- CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
Remediation/Fixing Recommendation:
- Implement strict input validation and parameterized queries.
- Use prepared statements to prevent SQL injection attacks.
- Regularly update the application and underlying libraries to ensure security patches are applied.
Cross-Site Scripting (XSS)
The Cross-Site Scripting vulnerability in the target system allows attackers to inject malicious scripts into web pages viewed by other users. This can lead to the theft of sensitive information, session hijacking, or distribution of malware. The vulnerability stems from inadequate input sanitization in user-generated content.
Proof of Concept (PoC):
- Input:
<script>alert('XSS Attack');</script> - Result: Display of a JavaScript alert on the victim's browser.
References:
Risk/Severity Scoring:
- CVSS Base Score: 6.3 (Medium)
- CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N
Remediation/Fixing Recommendation:
- Employ output encoding when rendering user-generated content.
- Implement Content Security Policy (CSP) to mitigate XSS attacks.
- Regularly audit and sanitize user inputs to prevent script injection.
Insecure Auth. & Session Management
The Insecure Authentication and Session Management vulnerability pose a critical risk to the target system's security. Insufficient enforcement of authentication controls and weak session management allow attackers to gain unauthorized access to user accounts, leading to data breaches and privacy violations.
Proof of Concept (PoC):
- Attacker: Exploits weak session management to gain unauthorized access to another user's account.
- Steps:
- Attacker logs into the application with their credentials.
- Attacker captures the session token generated upon successful authentication.
- Attacker sends the captured session token to a victim user via a crafted link.
- Victim user clicks the link and unknowingly shares their session token.
- Attacker uses the stolen session token to access the victim user's account.
References:
Risk/Severity Scoring:
- CVSS Base Score: 9.8 (Critical)
- CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
Remediation/Fixing Recommendation:
- Implement strong authentication mechanisms (e.g., multi-factor authentication).
- Store session tokens securely and set proper expiration periods.
- Regularly audit and monitor authentication and session management processes.
Directory Traversal
The Directory Traversal vulnerability allows attackers to navigate beyond the intended directory structure and access sensitive files or directories on the target system. Insufficient input validation and sanitization of user-provided data are common causes of this vulnerability.
Proof of Concept (PoC):
- Attacker: Exploits the directory traversal vulnerability to access a sensitive configuration file.
- Steps:
- Attacker provides a crafted input, such as
../../../etc/passwd. - Application improperly processes the input, leading to the traversal.
- Attacker gains access to the
/etc/passwdfile and extracts sensitive information.
- Attacker provides a crafted input, such as
References:
Risk/Severity Scoring:
- CVSS Base Score: 7.2 (High)
- CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H
Remediation/Fixing Recommendation:
- Implement strict input validation and filtering for user-provided data.
- Use whitelisting to restrict file paths and prevent directory traversal attacks.
- Keep sensitive files outside the web root directory to limit exposure.
Command Injection
The Command Injection vulnerability arises when user-supplied data is executed as a command without proper validation. Attackers can exploit this vulnerability to execute arbitrary commands on the target system, potentially leading to remote code execution.
Proof of Concept (PoC):
- Attacker: Exploits the command injection vulnerability to execute arbitrary commands.
- Steps:
- Attacker provides a malicious input, such as
; ls -la. - Application appends the input to a command without proper validation.
- Attacker gains the ability to execute the
ls -lacommand on the server.
- Attacker provides a malicious input, such as
References:
- OWASP Command Injection
- CWE-78: Improper Neutralization of Special Elements used in an OS Command ('OS Command Injection')
Risk/Severity Scoring:
- CVSS Base Score: 9.0 (Critical)
- CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H
Remediation/Fixing Recommendation:
- Avoid using user inputs directly in commands.
- Implement input validation and sanitization to prevent command injection.
- Use security mechanisms like Web Application Firewalls (WAF) to detect and block malicious inputs.
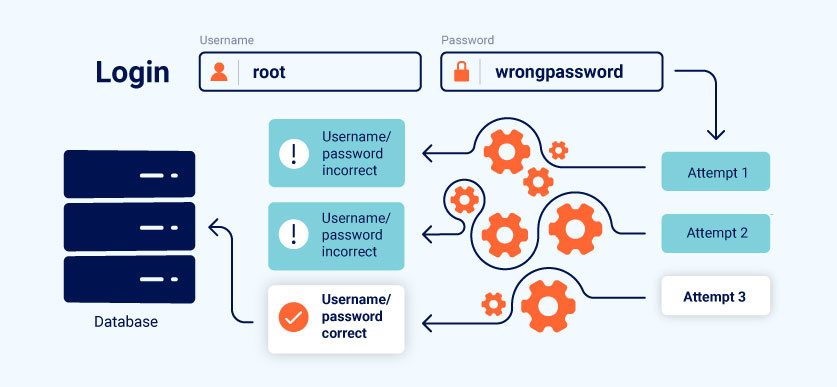
Business Logic
Business Logic Vulnerabilities involve flaws in the design or implementation of the application's logic. Attackers exploit these vulnerabilities to bypass intended restrictions, manipulate transactions, or gain unauthorized access to resources.
Proof of Concept (PoC):
- Attacker: Exploits a business logic vulnerability to escalate privileges.
- Steps:
- Attacker identifies a scenario where a user should have limited access.
- Attacker manipulates parameters or actions to gain unauthorized access.
- Attacker gains access to sensitive functionality, such as administrative controls.
References:
Risk/Severity Scoring:
- CVSS Base Score: 7.5 (High)
- CVSS Vector: CVSS:3.1/AV:N/AC:H/PR:N/UI:R/S:C/C:H/I:H/A:H
Remediation/Fixing Recommendation:
- Review and validate business logic flows for potential vulnerabilities.
- Implement access controls and authorization checks consistently.
- Use threat modeling to identify and address business logic vulnerabilities.
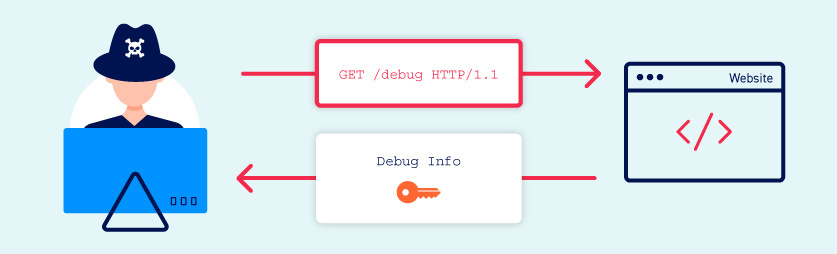
Information Disclosure
The Information Disclosure vulnerability exposes sensitive information, such as system details, error messages, or confidential data, to unauthorized users. Inadequate error handling and improper data protection contribute to this vulnerability.
Proof of Concept (PoC):
- Attacker: Exploits an information disclosure vulnerability to obtain sensitive server details.
- Steps:
- Attacker intentionally triggers an error condition on the application.
- Application responds with a verbose error message containing server information.
- Attacker gains insights into the server's technology stack and configuration.
References:
- OWASP Information Disclosure
- CWE-497: Exposure of Sensitive System Information to an Unauthorized Control Sphere
Risk/Severity Scoring:
- CVSS Base Score: 5.0 (Medium)
- CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:N/A:N
Remediation/Fixing Recommendation:
- Implement proper error handling to avoid revealing sensitive information.
- Configure security headers to restrict information leakage in responses.
- Regularly review and update error handling mechanisms.
Access Control
Access Control vulnerabilities occur when improper restrictions or validations allow unauthorized users to access restricted functionality or data. Flaws in authorization mechanisms contribute to this vulnerability.
Proof of Concept (PoC):
- Attacker: Exploits an access control vulnerability to access a privileged function.
- Steps:
- Attacker crafts a request to access a privileged endpoint, bypassing authorization.
- Application fails to enforce proper access controls, allowing the attacker to proceed.
- Attacker gains unauthorized access to administrative functions.
References:
Risk/Severity Scoring:
- CVSS Base Score: 8.2 (High)
- CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H
Remediation/Fixing Recommendation:
- Implement robust access controls based on roles and permissions.
- Conduct thorough authorization testing to ensure proper enforcement.
- Regularly review and update access control configurations.
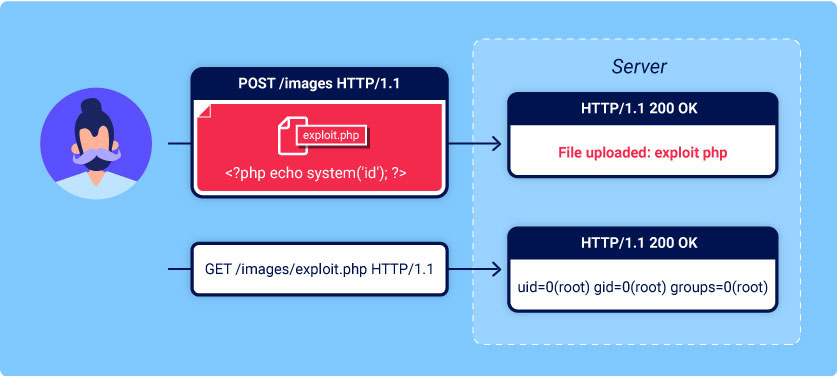
File Upload
File Upload vulnerabilities arise when inadequate validation and improper handling of user-uploaded files allow attackers to upload malicious files. This can lead to remote code execution, denial of service, or unauthorized data access.
Proof of Concept (PoC):
- Attacker: Exploits a file upload vulnerability to upload and execute a malicious script.
- Steps:
- Attacker crafts a malicious file with executable code (e.g., PHP shell).
- Attacker uploads the malicious file to the application.
- Application fails to properly validate the file and stores it in a publicly accessible location.
- Attacker accesses the malicious file and gains remote code execution.
References:
Risk/Severity Scoring:
- CVSS Base Score: 9.5 (Critical)
- CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H
Remediation/Fixing Recommendation:
- Implement strict file type validation and content inspection.
- Store uploaded files in a secure and non-executable location.
- Use server-side mechanisms to prevent execution of uploaded files.
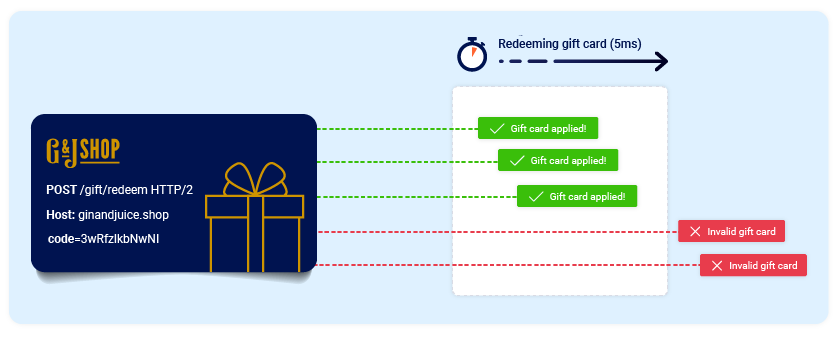
Race Conditions
Race Conditions vulnerabilities occur when multiple threads or processes compete to access shared resources simultaneously. Attackers exploit these vulnerabilities to manipulate the timing of operations and gain unauthorized access or privileges.
Proof of Concept (PoC):
- Attacker: Exploits a race conditions vulnerability to gain unauthorized access to a privileged operation.
- Steps:
- Attacker initiates multiple parallel requests targeting the same resource.
- Application's race condition leads to improper synchronization and timing issues.
- Attacker's request is processed inappropriately, granting unauthorized access.
References:
Risk/Severity Scoring:
- CVSS Base Score: 6.8 (Medium)
- CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:C/C:H/I:H/A:N
Remediation/Fixing Recommendation:
- Implement proper synchronization and locking mechanisms.
- Avoid using shared resources without proper safeguards.
- Regularly audit and monitor the application for race conditions.
Server-side Request Forgery (SSRF)
Server-side Request Forgery (SSRF) vulnerabilities allow attackers to make arbitrary requests from the server to external resources. Attackers exploit this vulnerability to perform port scanning, interact with internal systems, and leak sensitive data.
Proof of Concept (PoC):
- Attacker: Exploits an SSRF vulnerability to access an internal network resource.
- Steps:
- Attacker provides a crafted URL pointing to an internal resource.
- Application's SSRF vulnerability allows the attacker's request to be executed.
- Attacker receives sensitive information from the internal resource.
References:
Risk/Severity Scoring:
- CVSS Base Score: 7.5 (High)
- CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H
Remediation/Fixing Recommendation:
- Implement input validation and whitelist-based URL filtering.
- Limit server requests to trusted and safe resources.
- Implement network-level controls to prevent internal network exposure.
XML External Entity (XXE)
XML External Entity (XXE) vulnerabilities occur when an application processes XML input without proper validation. Attackers exploit these vulnerabilities to read files, perform internal port scanning, or launch denial of service attacks.
Proof of Concept (PoC):
- Attacker: Exploits an XXE vulnerability to access sensitive data from the server.
- Steps:
- Attacker crafts a malicious XML input containing an external entity reference.
- Application processes the XML input and includes the external entity.
- Attacker receives the content of a sensitive file in the response.
References:
Risk/Severity Scoring:
- CVSS Base Score: 8.2 (High)
- CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H
Remediation/Fixing Recommendation:
- Disable external entity processing in XML parsers.
- Use safe and validated parsers that block external entity references.
- Regularly update XML parsers and libraries to the latest secure versions.
Cross-site Request Forgery (CSRF)
Cross-site Request Forgery (CSRF) vulnerabilities allow attackers to trick users into performing unintended actions on a web application. Attackers exploit this vulnerability to manipulate user sessions and execute actions on behalf of the victim.
Proof of Concept (PoC):
- Attacker: Exploits a CSRF vulnerability to change the victim user's account password.
- Steps:
- Attacker crafts a malicious web page that contains a hidden form to change the password.
- Victim user, logged into the target application, visits the attacker's page.
- The hidden form is submitted on the victim's behalf, changing their password.
References:
Risk/Severity Scoring:
- CVSS Base Score: 6.1 (Medium)
- CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N
Remediation/Fixing Recommendation:
- Implement anti-CSRF tokens to validate user actions.
- Ensure that critical actions require user confirmation and authorization.
- Regularly review and update CSRF protections.
Cross-Origin Resource Sharing (CORS)
Cross-Origin Resource Sharing (CORS) vulnerabilities occur when an application does not properly control which origins can access its resources. Attackers exploit this vulnerability to perform unauthorized cross-origin requests and access sensitive data.
Proof of Concept (PoC):
- Attacker: Exploits a CORS vulnerability to steal sensitive data from another domain.
- Steps:
- Attacker hosts a malicious website on domain "evil.com."
- Victim visits a legitimate website on domain "victim.com" that is vulnerable to CORS.
- Attacker's website sends a cross-origin request to "victim.com" and steals data.
References:
- OWASP Cross-Origin Resource Sharing (CORS)
- CWE-942: Permissive Cross-domain Policy with Untrusted Domains
Risk/Severity Scoring:
- CVSS Base Score: 4.3 (Medium)
- CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N
Remediation/Fixing Recommendation:
- Implement proper CORS headers to restrict allowed origins.
- Use whitelisting to control which origins can access sensitive resources.
- Regularly review and update CORS configurations.
Clickjacking (UI Redressing)
Clickjacking vulnerabilities occur when attackers overlay or deceive users into interacting with hidden or opaque elements on a web page. Attackers exploit this vulnerability to trick users into performing actions without their consent.
Proof of Concept (PoC):
- Attacker: Exploits a clickjacking vulnerability to trick a user into performing an unintended action.
- Steps:
- Attacker creates an invisible iframe and positions it over a button on a legitimate site.
- Victim user visits the legitimate site and clicks the seemingly visible button.
- In reality, the user clicks the attacker's hidden iframe, performing an unwanted action.
References:
- OWASP Clickjacking (UI Redressing)
- CWE-1021: Improper Restriction of Rendered UI Layers or Frames
- CAPEC-103: Clickjacking
Risk/Severity Scoring:
- CVSS Base Score: 4.7 (Medium)
- CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:N/I:H/A:N
Remediation/Fixing Recommendation:
- Implement frame-busting techniques to prevent clickjacking.
- Use the X-Frame-Options header or Content Security Policy (CSP) to restrict framing.
- Educate users to be cautious while interacting with embedded content.
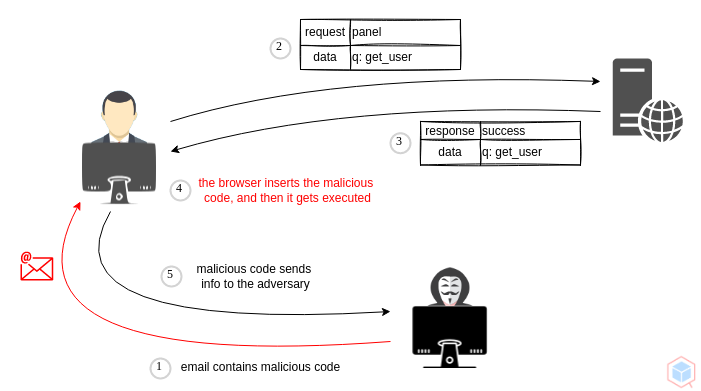
DOM-based Cross-Site Scripting (XSS)
DOM-based Cross-Site Scripting (XSS) vulnerabilities occur when untrusted data is used to manipulate the Document Object Model (DOM) in a web page. Attackers exploit this vulnerability to execute malicious scripts within the victim's browser.
Proof of Concept (PoC):
- Attacker: Exploits a DOM-based XSS vulnerability to execute a script on the victim's browser.
- Steps:
- Attacker crafts a URL with a payload that modifies the DOM on the victim's browser.
- Victim user clicks the malicious link and the payload executes in their browser.
References:
- OWASP DOM-based Cross-Site Scripting (XSS)
- CWE-79: Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting')
- CAPEC-588: DOM-Based XSS
Risk/Severity Scoring:
- CVSS Base Score: 6.5 (Medium)
- CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N
Remediation/Fixing Recommendation:
- Use context-aware output encoding when inserting data into the DOM.
- Implement Content Security Policy (CSP) to mitigate XSS attacks.
- Regularly audit and sanitize user inputs to prevent script injection.
WebSockets
WebSockets Security vulnerabilities occur when improper validation and authorization checks are applied to WebSocket connections. Attackers exploit this vulnerability to perform attacks such as data leakage or unauthorized access.
Proof of Concept (PoC):
- Attacker: Exploits a WebSockets Security vulnerability to perform unauthorized actions.
- Steps:
- Attacker establishes a WebSocket connection to the target application.
- Application fails to enforce proper authorization and access controls.
- Attacker sends messages that trigger unauthorized actions on the server.
References:
Risk/Severity Scoring:
- CVSS Base Score: 7.8 (High)
- CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H
Remediation/Fixing Recommendation:
- Implement strong authentication and authorization mechanisms for WebSocket connections.
- Regularly monitor WebSocket traffic and apply access controls.
- Keep WebSocket libraries and components up-to-date with security patches.
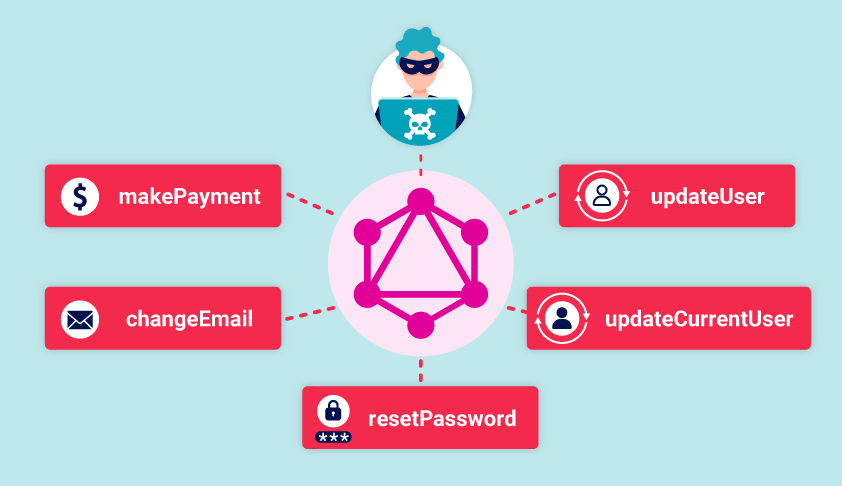
GraphQL API
GraphQL API vulnerabilities arise from improper access controls, query validation, and data exposure in GraphQL endpoints. Attackers exploit these vulnerabilities to execute arbitrary queries, perform data enumeration, or escalate privileges.
Proof of Concept (PoC):
- Attacker: Exploits a GraphQL API vulnerability to retrieve unauthorized data.
- Steps:
- Attacker crafts a malicious GraphQL query to access sensitive data.
- Application fails to enforce proper authorization and query validation.
- Attacker successfully extracts sensitive user information.
References:
Risk/Severity Scoring:
- CVSS Base Score: 8.0 (High)
- CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H
Remediation/Fixing Recommendation:
- Implement proper access controls and authentication mechanisms for GraphQL APIs.
- Validate and sanitize user inputs in GraphQL queries.
- Regularly review and update GraphQL schema and query validation.
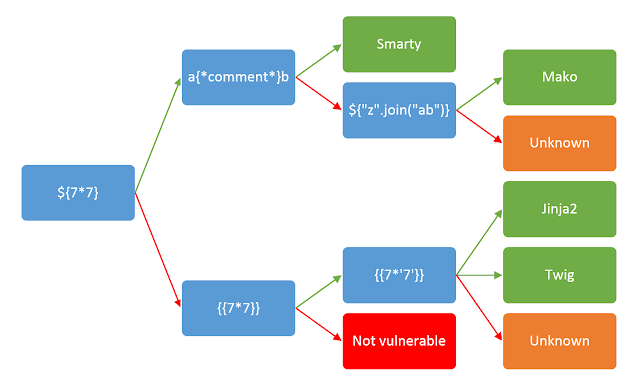
Server-side Template Injection (SSTI)
Server-side Template Injection (SSTI) vulnerabilities occur when user inputs are embedded directly into templates processed on the server. Attackers exploit this vulnerability to execute arbitrary code and gain unauthorized access.
Proof of Concept (PoC):
- Attacker: Exploits an SSTI vulnerability to execute arbitrary code on the server.
- Steps:
- Attacker injects a payload into a template variable.
- Application processes the template and evaluates the payload as code.
- Attacker's payload executes arbitrary code on the server.
References:
- OWASP Server-side Template Injection (SSTI)
- CWE-1336: Improper Neutralization of Special Elements Used in a Template Engine
Risk/Severity Scoring:
- CVSS Base Score: 8.8 (High)
- CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H
Remediation/Fixing Recommendation:
- Avoid interpolating user inputs directly into templates.
- Use safe template engines that automatically escape user inputs.
- Regularly update template engines to the latest secure versions.
Web Cache Poisoning
Web Cache Poisoning vulnerabilities occur when malicious content is cached and served to unsuspecting users. Attackers exploit this vulnerability to serve malicious content, manipulate user sessions, or launch phishing attacks.
Proof of Concept (PoC):
- Attacker: Exploits a web cache poisoning vulnerability to serve malicious content.
- Steps:
- Attacker injects a payload into a request parameter or URL.
- Application fails to validate or sanitize the input, causing caching of the malicious content.
- Future users visiting the cached page are exposed to the attacker's payload.
References:
Risk/Severity Scoring:
- CVSS Base Score: 7.2 (High)
- CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H
Remediation/Fixing Recommendation:
- Validate and sanitize user inputs before processing and caching.
- Set proper caching headers and strategies to minimize cache poisoning risks.
- Regularly review and clear cached content to prevent exposure to malicious payloads.
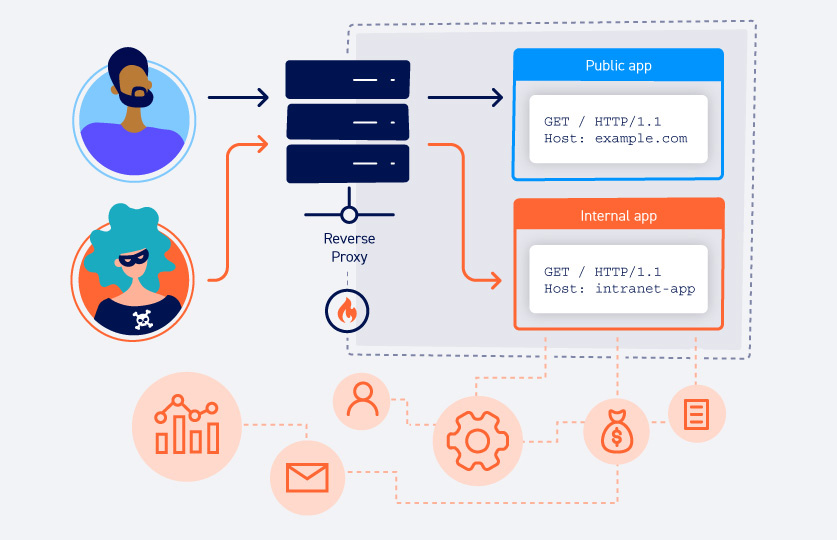
HTTP Host Header Attacks
Description: HTTP Host Header attacks exploit misconfigured web servers that rely on the Host header to determine the intended destination. Attackers exploit this vulnerability to redirect users to malicious sites or gain unauthorized access.
Proof of Concept (PoC):
- Attacker: Exploits an HTTP Host Header attack to redirect users to a malicious site.
- Steps:
- Attacker crafts a request with a manipulated Host header pointing to the malicious site.
- Application processes the request and redirects the user to the attacker's site.
References:
Risk/Severity Scoring:
- CVSS Base Score: 5.7 (Medium)
- CVSS Vector: CVSS:3.1/AV:N/AC:H/PR:N/UI:R/S:C/C:N/I:L/A:N
Remediation/Fixing Recommendation:
- Validate and sanitize input values used in redirection logic.
- Use whitelisting for allowed redirection destinations.
- Implement proper security controls to prevent host header manipulation.
HTTP Request Smuggling
HTTP Request Smuggling vulnerabilities occur due to discrepancies in how proxy servers and web servers handle and interpret HTTP requests. Attackers exploit this vulnerability to manipulate requests and perform actions on behalf of other users.
Proof of Concept (PoC):
- Attacker: Exploits an HTTP Request Smuggling vulnerability to bypass security controls.
- Steps:
- Attacker crafts specially crafted requests with conflicting headers.
- Proxy server and web server interpret requests differently, leading to request smuggling.
- Attacker's malicious payload is executed by the web server.
References:
Risk/Severity Scoring:
- CVSS Base Score: 8.6 (High)
- CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H
Remediation/Fixing Recommendation:
- Ensure consistent interpretation of headers between proxy and web server.
- Implement security mechanisms to detect and prevent request smuggling.
- Regularly update proxy and web server software to mitigate vulnerabilities.
OAuth 2.0 Authentication
OAuth 2.0 authentication vulnerabilities arise from improper implementation of the OAuth 2.0 framework. Attackers exploit these vulnerabilities to gain unauthorized access to user accounts, impersonate users, or obtain unauthorized tokens.
Proof of Concept (PoC):
- Attacker: Exploits an OAuth 2.0 authentication vulnerability to steal user tokens.
- Steps:
- Attacker crafts a malicious application and tricks users into authorizing it.
- Malicious application receives authorization code or token.
- Attacker gains unauthorized access to the victim's account or token.
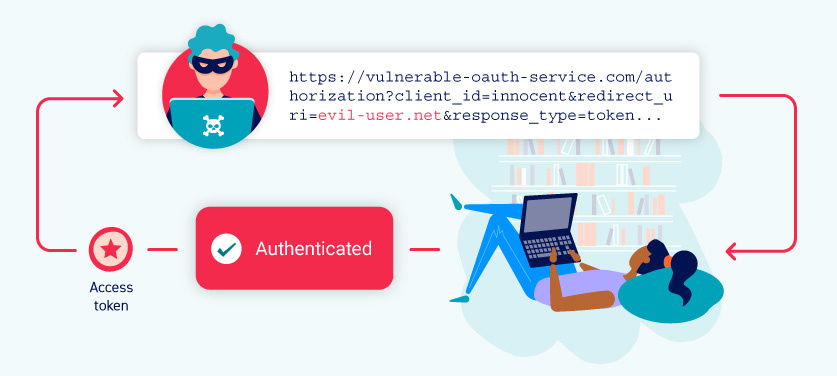
References:
Risk/Severity Scoring:
- CVSS Base Score: 7.9 (High)
- CVSS Vector: CVSS:3.1/AV:N/AC:H/PR:N/UI:R/S:U/C:H/I:H/A:H
Remediation/Fixing Recommendation:
- Implement OAuth 2.0 securely with appropriate grant types.
- Validate and sanitize authorization callbacks to prevent open redirects.
- Regularly audit and monitor OAuth 2.0 authorization flows.
JWT (JSON Web Token) Attacks
JWT (JSON Web Token) attacks exploit vulnerabilities in the generation, validation, and usage of JWTs. Attackers exploit these vulnerabilities to bypass authentication, impersonate users, or gain unauthorized access.
Proof of Concept (PoC):
- Attacker: Exploits a JWT vulnerability to gain unauthorized access.
- Steps:
- Attacker crafts a malicious JWT with altered claims or tokens.
- Application fails to properly validate the JWT, allowing the attacker's token.
- Attacker gains access to resources or impersonates a user.
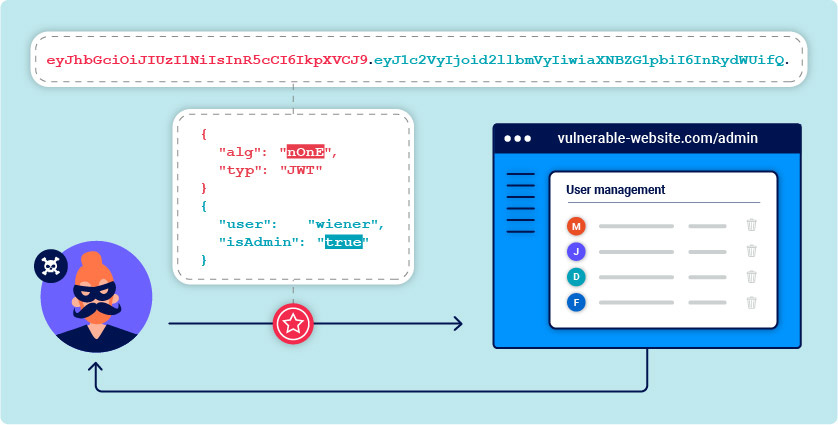
References:
Risk/Severity Scoring:
- CVSS Base Score: 7.2 (High)
- CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H
Remediation/Fixing Recommendation:
- Use strong algorithms and keys for JWT generation and verification.
- Validate and sanitize JWT claims and tokens on both sides.
- Implement JWT expiration and refresh mechanisms securely.
Prototype Pollution
Prototype Pollution vulnerabilities occur when attackers manipulate the prototype of objects in JavaScript code. Attackers exploit this vulnerability to inject malicious properties or modify existing ones, leading to remote code execution or denial of service.
Proof of Concept (PoC):
- Attacker: Exploits a Prototype Pollution vulnerability to inject malicious properties.
- Steps:
- Attacker crafts input to manipulate JavaScript objects' prototypes.
- Application processes the input, leading to modification of object properties.
- Attacker's malicious properties are executed, leading to code execution.
References:
- OWASP Prototype Pollution
- CWE-1321: Improperly Controlled Modification of Object Prototype Attributes ('Prototype Pollution')
Risk/Severity Scoring:
- CVSS Base Score: 8.9 (High)
- CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H
Remediation/Fixing Recommendation:
- Avoid using untrusted input to modify object prototypes.
- Implement input validation and sanitation to prevent prototype pollution.
- Regularly update and patch JavaScript libraries to prevent vulnerabilities.
Conclusion
This assessment highlights critical vulnerabilities within the target system, which can potentially compromise data integrity, user privacy, and overall system security. The findings underscore the importance of proactive security practices, including robust input validation, secure authentication mechanisms, and ongoing vulnerability management. Implementing the recommended remediation steps is crucial to safeguard the target system and its users from potential threats.
How am I doing?
Hey! Lemme know if you found this helpful by leaving a reaction.
- x0
- x0
- x0
- x0
- x0
- x0
- x0
Loading














